BSidesCTF zumbo2 challenge
Welcome to ZUMBOCOM….you can do anything at ZUMBOCOM.
Three flags await. Can you find them?
http://zumbo-8ac445b1.ctf.bsidessf.net
Stage 3 - coming soon!
This was part 2 of another Web challenge, zumbo1. A teammate, Lukhvir Athwal, had discovered the source code for server.py in part 1. From this code, I saw that flag 2 was in a local file and the script was using the flask library.
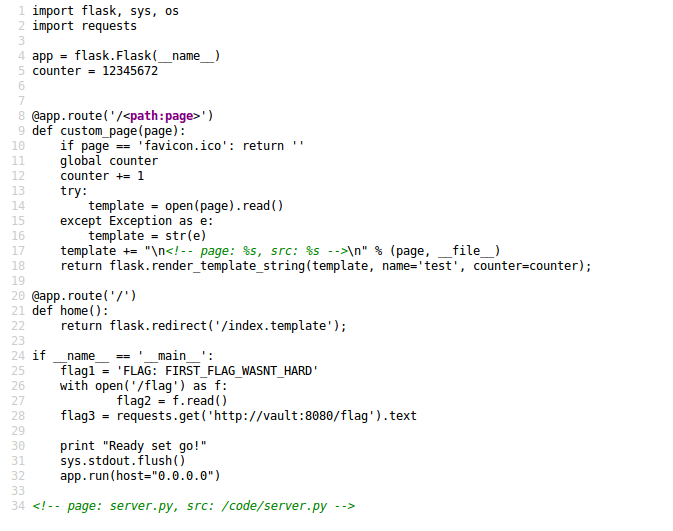
One thing that immediately raised a flag was the commented out line at the bottom of the source. This line could be controlled by the user so I tested to see if it was vulnerable to cross-site scripting.
http://zumbo-8ac445b1.ctf.bsidessf.net/--><script> alert(1)</script><!--The page was vulnerable to cross-site scripting but there seemed to be better approaches to this challenge.
A quick google search for “flask vulnerabilites” showed me that this page may be susceptible to Server Side Template Injection(SSTI). This was a new technique for me but I found two very helpful articles.
- https://nvisium.com/blog/2016/03/09/exploring-ssti-in-flask-jinja2/
- https://nvisium.com/blog/2016/03/11/exploring-ssti-in-flask-jinja2-part-ii/
I highly suggest reading these articles. They provide a great explanation about template injection vulnerabilities and how to test and exploit them.
The article mentions that pages vulnerable to cross-site scripting are often vulnerable to SSTI. To test this vulnerability they suggest entering {{ 7 * 7 }} into the vulnerable field.
http://zumbo-8ac445b1.ctf.bsidessf.net/{{ 7 * 7 }}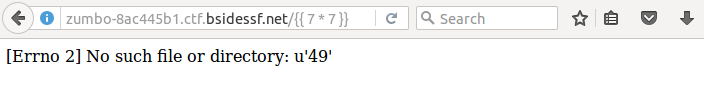
Since the server returned 49 I know it is vulnerable. I just needed to use this to read the local file ./flag.
The second article above gives a great explanation of how to use this exploit to read local files. Essentially, I can access any class in the current python environment and here I use the file class.
I instantiated a class of type ‘file’ and call the read() method. Read the article for a better explanation.
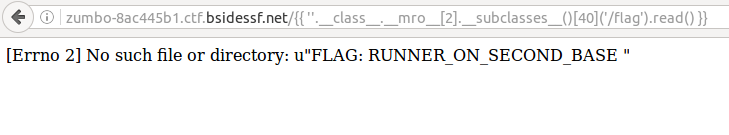
FLAG:RUNNER_ON_SECOND_BASE
**I was unable to solve Zumbo 3 but I was on the right path. I was trying to use this exploit with a payload to make a get request to ‘http://vault:8080/flag’.
Unfortunately, I focused on the request library and should have looked at other options.
I have listed two writeups below for references.